Brilliant Info About How To Check If Your Computer Is Infected With Conficker

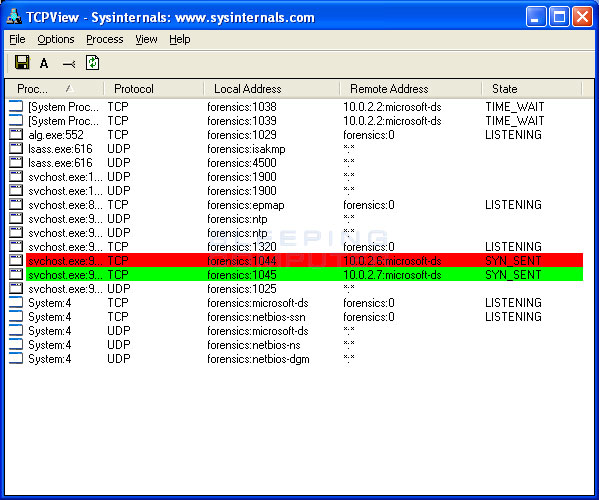
The latest version of nmap has the ability to detect all (current) variants of conficker by detecting the otherwise almost invisible changes that the worm makes to the port 139.
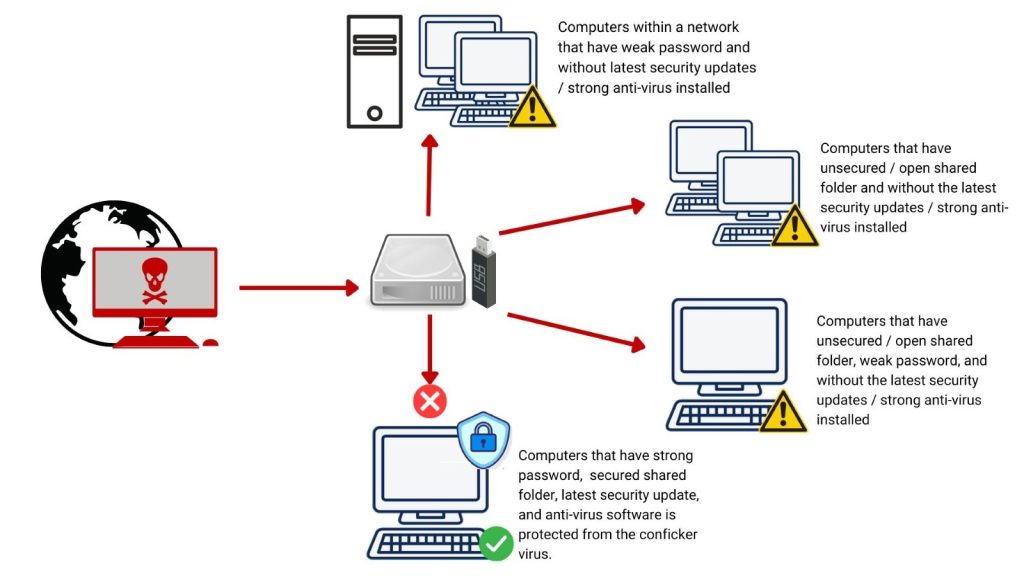
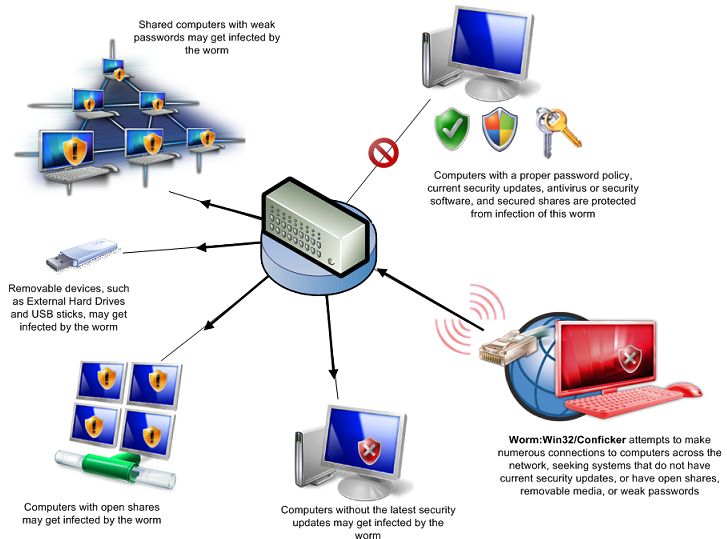
How to check if your computer is infected with conficker. The conficker working group has developed a great visual resource to help folks instantly check to see if their systems are infected. So how do you know if your computer is infected with conficker and, more importantly, what should you do if it is? A quick visual scan can tell you whether you're infected with the conficker worm or similar malware.
Attempts to estimate the populations of conficker infected hosts at any given time have varied widely, but all estimates exceed millions of personal computers. On the quarantine page you can see which threats were. Ignore the ones that complain.
Support for windows vista service pack 1 (sp1) ends on july 12, 2011. Important services are disabled on your computer. The conficker working group is offering a quick, simple way to check that your pc is free of the conficker worm.
Researchers find flaw in conficker that lets them detect which computers have the legitimate microsoft patch and which. Find the computers that are not complaining about it. A quick way to determine if a computer is infected with conficker.
Conficker flaw reveals which computers are infected. One fast way to check is to try to visit any major security software publisher's web site. Only windows pc users should be concerned (people who use macs or other operating systems are not vulnerable).
Choose the scan + quarantine option. There are a few tools that you can use to track and find conficker infected computers on your network. Afterwards you can check the detections page to see which threats were found.
First, check whether you are infected. If you can see all 6 images,. To continue receiving security updates for windows, make sure you're running windows vista with service pack 2 (sp2).
The computers that are infected with conficker will not have working. Security event logs network monitoring tools firewalls with logging (i.e.,. By gregg keizer senior reporter, computerworld | mar 30, 2009 1:58 pm pst just days before the conficker worm is set to contact its controllers for new.